Q. Is this really as harmful as you think?
A. Go to your parents house, your grandparents house etc and look at their Windows PC, look at the installed software in the past year, and try to use the device. Run some antivirus scans. There’s no way this implementation doesn’t end in tears — there’s a reason there’s a trillion dollar security industry, and that most problems revolve around malware and endpoints.


Did you read the article?
This system basically do a character recognition on EVERYTHING the user is displaying and save the results in a very small file not that well protected.
The data is very small (I guess because it’s basically text?), seems easy to find. That means the history of all you did on your computer (apparently only for the last three feays by default,but well…) can be stolen at once, in a minuscule file.
I’m not an IT specialist, but I don’t see in which world this can remotely be a good idea…
As I understand not everything will be read and stored, storage will be encrypted. We don’t even know what exactly will be stored and everybody here is losing their mind.
We already have a lot of sensitive information on our computers and nobody is panicking.
I guess it’s hard to get used to new stuff. Or maybe Linux users are afraid that their favourite system won’t be able to compete anymore.
You didn’t read the article.
We do know the answers to these questions. And if I can use a 2 line script to exfiltrate all your screen data for days/weeks in under a few MB of data.
So better hope you, never, ever, ever run unauthorized or malicious code, because now it basically has a honeypot of top priority data, always stored in a known location and compressed for easy uploads.
What kind of malicious code would be able to do that?
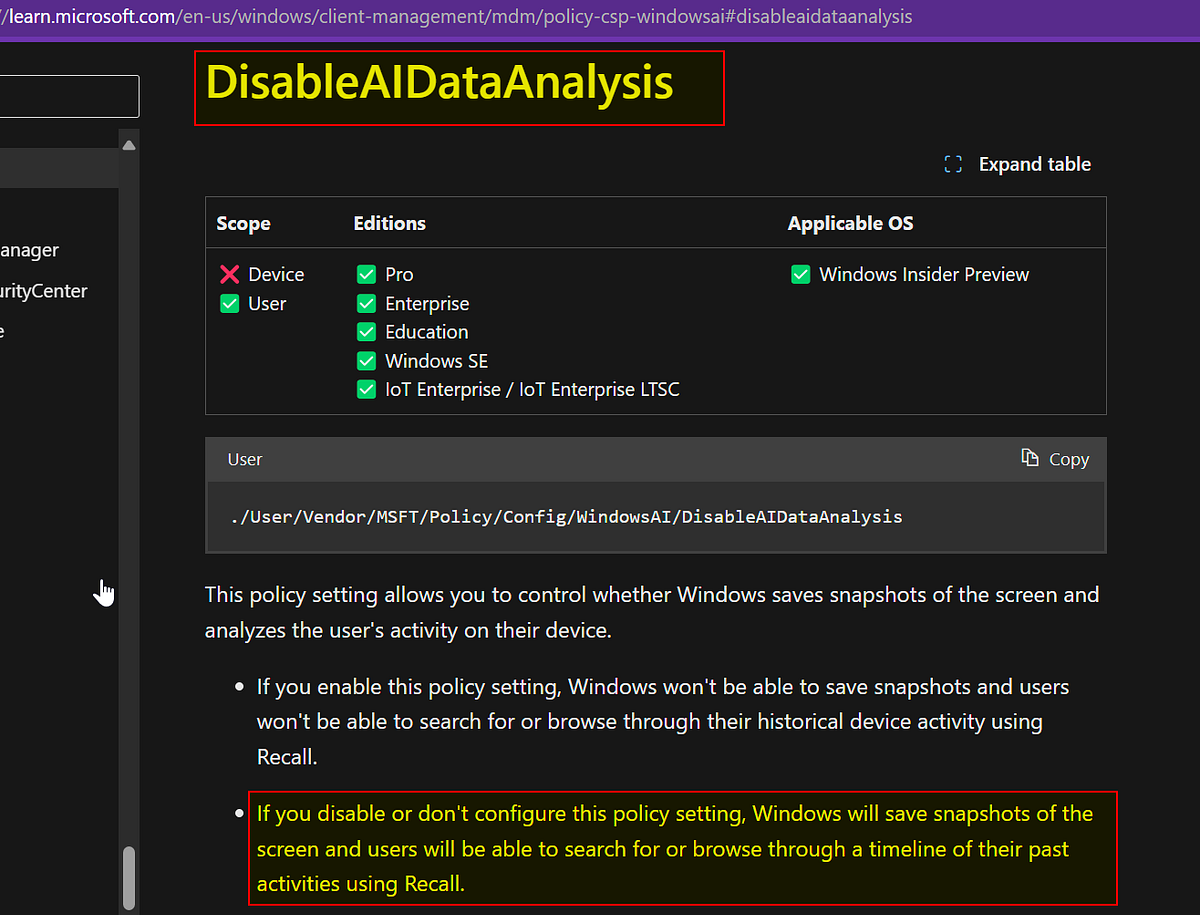
Q. The data is processed entirely locally on your laptop, right? A. Yes! They made some smart decisions here, there’s a whole subsystem of Azure AI etc code that process on the edge. Q. Cool, so hackers and malware can’t access it, right? A. No, they can. Q. But it’s encrypted. A. When you’re logged into a PC and run software, things are decrypted for you. Encryption at rest only helps if somebody comes to your house and physically steals your laptop — that isn’t what criminal hackers do. For example, InfoStealer trojans, which automatically steal usernames and passwords, are a major problem for well over a decade — now these can just be easily modified to support Recall. Q. But the BBC said data cannot be accessed remotely by hackers. A. They were quoting Microsoft, but this is wrong. Data can be accessed remotely. Q. Microsoft say only that user can access the data. A. This isn’t true, I can demonstrate another user account on the same device accessing the database. Q. So how does it work? A. Every few seconds, screenshots are taken. These are automatically OCR’d by Azure AI, running on your device, and written into an SQLite database in the user’s folder. This database file has a record of everything you’ve ever viewed on your PC in plain text. OCR is a process of looking an image, and extracting the letters. Q. What does the database look like? A:https://twitter.com/GossiTheDog/status/1796218726808748367?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1796218726808748367%7Ctwgr%5E2eccf634534245a77c4f931d8722f1b8c6f23595%7Ctwcon%5Es1_&ref_url=https%3A%2F%2Fcdn.embedly.com%2Fwidgets%2Fmedia.html%3Ftype%3Dtext2Fhtmlkey%3Da19fcc184b9711e1b4764040d3dc5c07schema%3Dtwitterurl%3Dhttps3A%2F%2Fx.com%2FGossiTheDog%2Fstatus%2F1796218726808748367image%3D Q. How do you obtain the database files? A. They’re just files in AppData, in the new CoreAIPlatform folder. Q. But it’s highly encrypted and nobody can access them, right?! A. Here’s a few second video of two Microsoft engineers accessing the folder: https://cyberplace.social/system/media_attachments/files/112/535/509/719/447/038/original/7352074f678f6dec.mp4 Q. …But, normal users don’t run as admins! A. According to Microsoft’s own website, in their Recall rollout page, they do: https://miro.medium.com/v2/resize:fit:1100/format:webp/0*WGE1jcRzhe6WAGQS In fact, you don’t even need to be an admin to read the database — more on that in a later blog. Q. But a UAC prompt appeared in that video, that’s a security boundary. A. According to Microsoft’s own website (and MSRC), UAC is not a security boundary: https://miro.medium.com/v2/resize:fit:1100/format:webp/1*TTjYNH15IoP_d8JhhG3cEA.png Q. So… where is the security here? A. They have tried to do a bunch of things but none of it actually works properly in the real world due to gaps you can drive a plane through. Q. Does it automatically not screenshot and OCR things like financial information? A. No: https://miro.medium.com/v2/resize:fit:1100/format:webp/1*OZMjujpALL3IfAQYT64x7Q.pngDo I have to continue or do you think you could actually read the article for the rest? It’s clearly a bigger deal than “linux users mad because windows better” and your poor excuse for a troll just makes it look like you’re too stupid to read the article laid out in front of you. Well, now you have no excuse so get good.
Sorry I don’t take everyones word as truth. This guy is just one guy. One guy against the whole Microsoft corporation whose entire fortune depends on this not to fail in the way he said it certainly will. Absurd.
Lol you’re hopeless.
Lol you believe everything lol.
Have fun with that.
Then don’t believe one guy, read the other reports on the feature, or the reports from Microsoft’s BUILD conference that confirm these details.
It’s stored in the appdata folder in plaintext.
Based on what Microsoft themselves said we know: everything will be stored (except edge private session…). They specifically say they don’t do content moderation: they log everything.
Did you read the article?
As a windows user I’m not delighted by this.
Edit: at this point you must be trolling…
If you are so afraid, you can just turn it of. You are aware of this are you not?
OK if you think I’m trolling, why did you answer?
I give you the benefit of the doubt you are a reasonable person who can go beyond their emotions of a feature of an os. And the emotions this article stirred.
Encryption at rest is meaningless if you get infected with spyware.