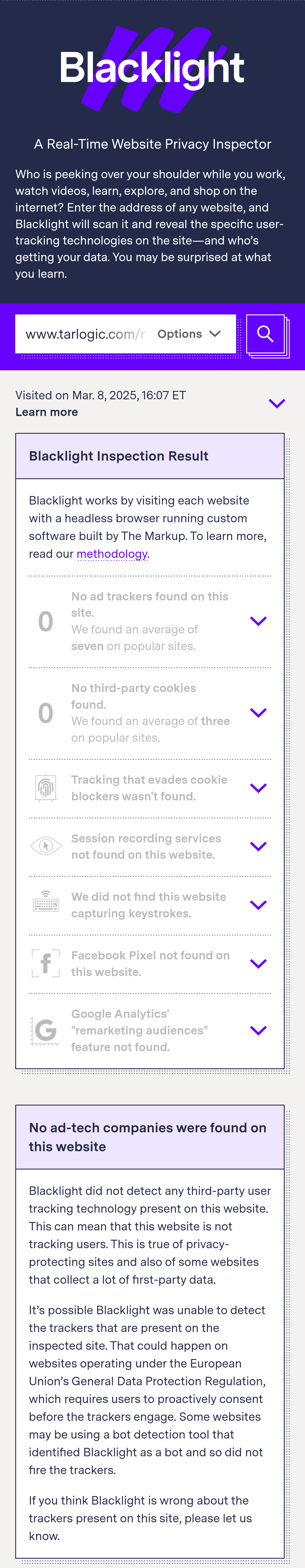
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


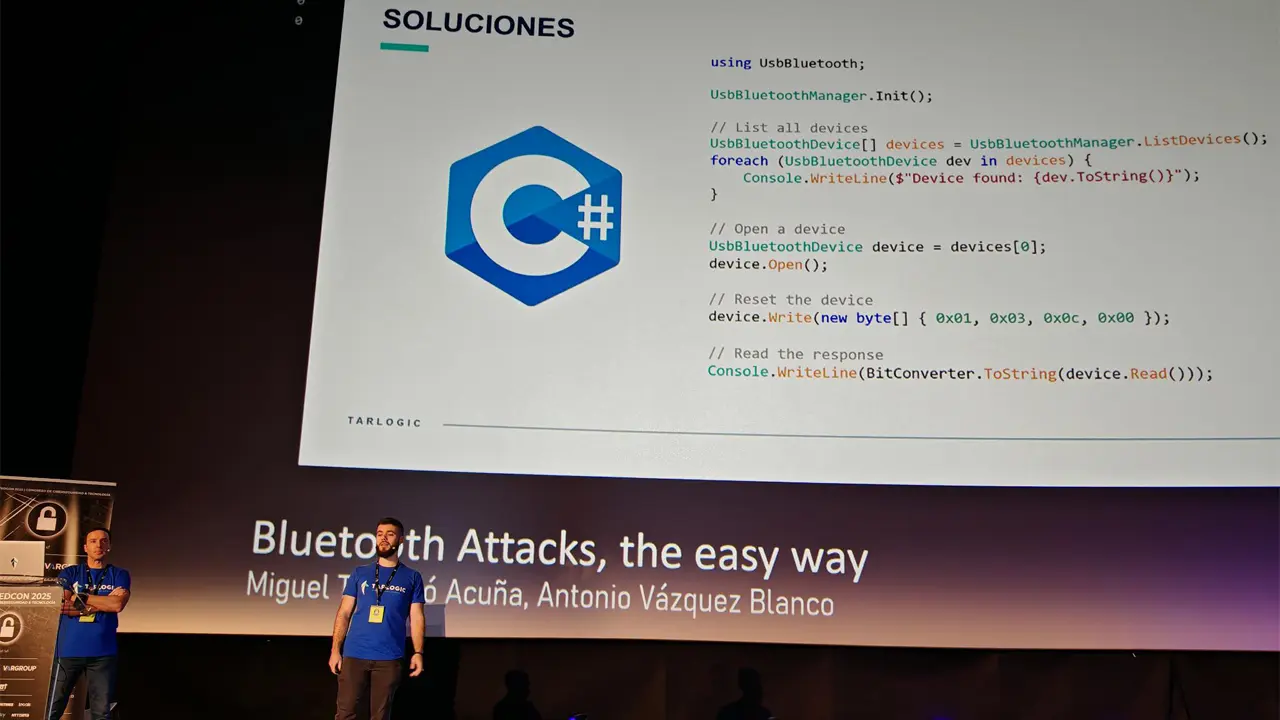
It ain’t so.
To use the “backdoor” an attacker needs to have full access to the esp32 powered device already.
It’s like claiming that being able to leave your desk without locking your PC is a backdoor in your OS.
Yes, this is about undocumented instructions found in the silicon but they are not executable unless the ESP32’s firmware uses them. Firmware cannot be edited to use them unless you have an existing vulnerability such as physical access or insecure OTA in existing firmware (as far as researchers know).
It is good to question the “backdoor” allegations - maybe the instructions’ microcode was buggy and they didn’t want to release it.